The 37 most important events in American cybersecurity history
I've never been one for remembering important dates and names. Many years ago, when the Edward Snowden leaks came out, I determined that someone was watching everything I did online, so I might as well know who they were and why they were doing it. Since then, I started writing down noteworthy events in the history of hacking, cybersecurity, and government oversight. This is not an exhaustive list of everyone and everything that has ever happened; this is a list by me, for me, to remember significant events.
1920
Herbert O. Yardley, the founder of the Black Chamber (a government agency that proceeds the NSA), convinces Newcomb Carlton, the president of Western Union, to grant him access to all telegraphs going through Western Union. The overreach of government oversight begins.
1945
The Soviet Union gifts The Thing, a secret electromagnetic listening device disguised within a commemorative plaque, to Averell Harriman, the U.S. Ambassador to the Soviet Union. British radio operators discover it in 1951. This is the first electromechanical bug ever discovered.
1967
The Supreme Court holds in Katz v. United States that the monitoring and recording of private conversations within the United States constitutes a "search" for Fourth Amendment purposes, and therefore requires a warrant. (Prior to this, the 1928 ruling from Olmstead v. The United States held that wiretapping a private phone conversation did not violate the Fourth Amendment.) This is the beginning of courts requiring police to obtain search warrants for telecommunications data.
1978
The NSA's eavesdropping on Vietnam War protesters and civil rights activists motivates Congress to pass the Foreign Intelligence Surveillance Act. This act requires the NSA to have search warrants approved by a secret F.I.S.A. court in order to spy on Americans. Domestic spying ends for a brief moment.
1979
The Supreme Court holds in Smith v. Maryland that a warrant is required for the government to acquire the content of electronic communications. However, only subpoenas are required for the business records (metadata) of these communications. "Metadata" includes the phone numbers that an individual has dialed, and the location of phone communications.
1985
During Project GUNMAN, the NSA finds a Soviet bug attached to a typewriter inside the U.S. embassy in Russia, capturing every keystroke. This is the second electromechanical bug ever discovered.

1986
Karl Koch, A German hacker, is caught selling hacked information from United States military computers to the KGB. This is the first known cyberattack by Russia on American soil.
The Electronic Communications Privacy Act of 1986 is enacted by Congress to extend restrictions on government wiretaps to include the transmission of electronic data.
1988
The Morris Worm takes down 60,000 computers. This is the first worm to take down more than 10% of the internet. Robert Morris Jr., the creator of the worm, is a fascinating individual: the son of NSA chief scientist Robert Morris Sr., he co-founds Y Combinator in 2005.
1996
The CIA’s CITO unit, the predecessor to the CIA's Information Operations Center, starts training spies to put NSA hardware – like spyware spiked microchips – in corporate supply chains.
1998
The CIH virus infects sixty million computers internationally, especially impacting countries that don't have widespread antivirus software. This virus hugely accelerates the awareness of the need for antivirus software.
2001
Congress passes the Patriot Act, allowing the U.S. government to store phone records, including call logs (but not recordings), along with internet activity and text messages, for purposes of antiterrorism.
The ILoveYou worm spreads globally. This is the first email worm to combine social engineering (who doesn't want to open an email that says "I love you"?) and a Windows vulnerability in order to spread quickly.
2002
Symantic buys Bugtraq, a public bug tracker, and makes it private. This is the beginning of private companies and governments paying hackers for exploits instead of publicizing known vulnerabilities. In 2007, Charles Miller, a security researcher, publishes a paper that reveals that government agencies like the NSA will pay hackers very high prices (usually $5,000 to $250,000) for discovering security vulnerabilities.
The Pentagon announces the Total Information Awareness project. Funding is cut off one year later, but the NSA continues to use its software to mine telephone conversations and web searches as part of Stellar Wind. This enables the NSA – with George W. Bush’s knowledge and consent – total, unsupervised access to all fiber-optic communications in the U.S. until 2004, when domestic communication data collection is deauthorized.
The NSA installs a listener in Room 641A of the San Francisco AT&T building – along with more than ten other telecom buildings across the country – to collect all metadata relating to NSA-provided search terms. This later becomes public knowledge in 2013 when Snowden reveals the existence of Project UPSTREAM.
2005
China begins its Titan Rain espionage attacks on the networks of NASA and Lockheed Martin. This is the beginning of Chinese hacking on American soil.
2007
Russia conducts DDOS cyberattacks on Estonia, marking the beginning of what cybersecurity researchers often refer to as Web War 1.
2008
The NSA deploys the Stuxnet worm to infiltrate an Iranian nuclear plant. This is the first cyberattack to use multiple zero days. (It uses four.)
The Foreign Intelligence Surveillance Act of 1978 Amendments Act of 2008 expands the government’s ability to conduct electronic surveillance domestically without court orders, basically codifying what the NSA has been doing illegally. Congress grants telecom officials immunity not only from prosecution but also from civil suits.
2009
Charlie Miller jailbreaks an iPhone, MacBook Air, and Android by directing users to a malicious website that allows him to see every keystroke. Google ignores his bug report so he starts a “no more free bugs” campaign. (In 2014, Google reverses its decision by starting Project Zero, an internal team that publicizes all bugs that Google knows about, and encourages other tech companies to do the same.)
2010
NSO, an Israeli cybersecurity firm that sells spyware – built using vulnerabilities found in popular mobile phone technologies like iPhone and Android – is founded. This is the beginning of the commercialization of the zero day industry.
2012
Iran deploys the Shamoon cyberattack on Saudi Aramco to retaliate for Stuxnet.
2013
Edward Snowden reveals that the NSA is storing U.S. citizens' phone records. His revelations unearth NSA programs like PRISM and MUSCULAR (which proved the NSA had hacked into Google without even Google knowing). A Pew report soon after the scandal shows that 46% of Americans are still not concerned about American surveillance.
Der Spiegel releases a report that NSA TAO unit hackers have developed a program called DROPOUTJEEP that allows the NSA to track every keystroke on an iPhone. Next, Der Spoegel publishes a 50 page list of NSA exploits that journalists call "way more revealing" than the Snowden leaks.
Under pressure after Snowden, the Foreign Intelligence Surveillance Court reveals that, in 2012 alone, it approved 1,748 of the 1,789 applications it received to survey Americans.
2014
Google finds a bug in SSL called Heartbleed that allows 17% of the internet’s web server’s private keys to be stolen. This is the first vulnerability to affect as much as 17% of the internet.
2016
A group of hackers calling themselves the “Shadow Brokers” leak several NSA zero days, thought to be stolen from the home of an NSA employee. This is the first time the NSA is publicly hacked. The next year, the Shadow Brokers leak one of the most virulent of these vulnerabilities, nicknamed Eternal Blue, which is then used in two subsequent worldwide cyberattacks: WannaCry (see below) and NotPetya (also below).
Russia hacks the Democratic National Committee through the famous John Podesta phishing email.
The F.B.I. buys a zero day to jailbreak the phone of the San Bernadino shooting suspects. This is the first time the F.B.I. publicly acknowledges paying for a zero day.
A North Korean hacking group steals $81 million from Bangladesh’s central bank. This increases public awareness of North Korea's hacking expertise; many say that North Korea trails only the U.S., Russia, and China in hacking capabilities.
2017
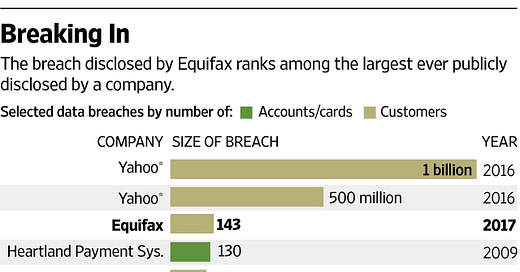
Chinese hackers commit the Equifax data breach.
Wannacry, built using Eternal Blue, shuts down the U.K. hospital system.
Russia conducts the NotPetya cyberattack on Ukraine (“Web War 2”) that cuts power across Ukraine in 5 hours. One year later, the U.S. Treasury announces sanctions against nineteen Russians organizations thought to be involved.
2018
NSO spyware called Pegasus is used to hack the phone of Jeff Bezos. His personal photos end up in the hands of the National Enquirer, which then threatens to blackmail him. In response, he releases the photos himself. This is the first scandal that puts NSO's phone hacking capabilities on the front page of the news.
2020
The SolarWinds cyberattack – likely the work of Russia's FSB security service – penetrates thousands of organizations globally, including multiple parts of the United States federal government. It spreads through these organizations via the Orion network management software, a product of SolarWinds. SolarWinds' development server's password was "solarwinds123," which allowed the hackers to get into the server and place malicious code in Orion's software toolchain. Brad Smith, President of Microsoft, calls it the "most sophisticated attack the world has ever seen.” He estimates that the attack required thousands of engineers to build and deploy.
2021
Russian hackers use an employee's leaked password to hack into Colonial Pipeline's servers, shutting down their servers until a ransom was paid. Since Colonial Pipeline supplies nearly half of the East Coast's liquid fuels, this becomes one of the most famous ransomware attacks on the United States. Luckily, Colonial Pipeline restores service within a day.
Sources
The Cuckoo's Egg (Clifford Stoll)
Sandworm (Andy Greenberg)
They Know Much More Than You Think, The New York Review (James Bamford)
This Is How They Tell Me the World Ends (Nicole Perlroth)
Unwarranted: Policing Without Permission (Barry Friedman)